Monitor all devices 24×7, receive real-time alerts, and take advantage of remote troubleshooting all in one place. The Meraki dashboard provides an intuitive, cloud-based interface to manage your entire network. Single client VPN would be particularly useful for clients utilizing mobile devices, laptops, as well as home desktop users. The Meraki Client VPN utilizes the native VPN client built into Windows, OS X, and iOS clients to name a few examples. Client VPN creates a tunnel from the client and forwards all VPN traffic through that tunnel to the MX.
The VPN:
The Meraki client VPN uses the L2TP tunneling protocol and can be deployed on PC’s, Mac’s, Android, and iOS devices without additional software as these operating systems natively support L2TP.
The Encryption Method:
Along with the L2TP/IP protocol the Meraki client VPN employs the following encryption and hashing algorithms: 3DES and SHA1 for Phase1, AES128/3DES and SHA1 for Phase 2. Best practice dictated that the shared secret should not contain special characters at the beginning or end.
Enabling Client VPN:
Select Enabled from the Client VPN server pull-down menu on the Security Appliance -> Configure -> Client VPN page. You can then configure the following options:

- Client VPN Subnet: The subnet that will be used for Client VPN connections. This should be a private subnet that is not in use anywhere else in your network. The MX will be the default gatway on this subnet and will route traffic to and from this subnet.
- DNS Nameservers: The servers VPN Clients will use to resolve DNS hostnames. You can choose from Google Public DNS, OpenDNS, or specifying custom DNS servers by IP address.
- WINS: If you want your VPN clients to use WINS to resolve NetBIOS names, select Specify WINS Servers from the drop-down and enter the IP addresses of the desired WINS servers.
- Secret: The shared secret that will be used to establish the Client VPN connection.
- Authentication: How VPN Clients will be authenticated.
- Systems Manager Sentry VPN Security: Configuration settings for whether devices enrolled in systems manager should receive a configuration to connect to the Client VPN.
Authentication:
The VPN uses both pre-shared key based authentication and user authentication. To set up the user authentication mechanism, you will need to select your authentication method.
Meraki Cloud Authentication:
Use this option if you do not have an Active Directory or RADIUS server, or if you wish to manager your VPN users via the Meraki cloud. To add or remove users, the User Management section at the bottom of the page. Add a user by selecting “Add new user” and entering the following information:
- Name: Enter the user’s name
- Email: Enter the user’s email address
- Password: Enter a password for the user or select “Generate” to automatically generate a password
- Authorized: Select whether this user is authorized to use the Client VPN
In order to edit an existing user, click on the user under User Management section. To delete a user, click the X next to the user on the right side of the user list. When using Meraki hosted authentication, the user’s email address is the username that is used for authentication.
RADIUS:
Use this option to authenticate users on a RADIUS server. Click Add a RADIUSserver to configure the server(s) to use. You will need to enter the IP address of the RADIUS server, the port to be used for RADIUS communication, and the shared secret for the RADIUS server.
Active Directory:
Use this option if you want to authenticate your users with Active Directory domain credentials. You will need to provide the following information:
- Short Domain: The short name of your Active Directory domain.
- Server IP: The IP address of an Active Directory server on the MX LAN.
- Domain Admin: The domain administrator account the MX should use to query the server.
- Password: Password for the domain administrator account.
For example, considering the following scenario: You wish to authenticate users in the domain test.company.com using an Active Directory server with IP 172.16.1.10. Users normally log into the domain using the format ‘test/username’ and you have created a domain administrator account with the username ‘vpnadmin’ and the password ‘vpnpassword’.
- The Short domain would be ‘test’.
- The Server IP would be 172.16.1.10
- The Domain admin would be ‘vpnadmin’
- The Password would be ‘vpnpassword’.
At this time, the MX does not support mapping group policies via Active Directory for users connecting through the Client VPN.
Systems Manager Sentry VPN Security:
When using Meraki cloud authentication, Systems Manager Sentry VPN security can be configured. If your Dashboard organization contains one or more MDM networks. Systems Manager Sentry VPN security allows for your devices enrolled in Systems Manager to receive the configuration to connect to the Client VPN through the Systems Manager profile on the device.
To enable Systems Manager Sentry VPN security, choose Enabled from the Client VPN server pulldown menu on the Security Appliance -> Configure -> Client VPN page. You can configure the following options:
- Install Scope: The install scope allows you to select a set of Systems Manager tags for a particular MDM network. Devices with these tags applied in a Systems Manager network will receive a configuration to connect to this network’s Client VPN server through their Systems Manager profile.
- Send All Traffic: Select whether all client traffic should be sent to the MX.
- Proxy: Whether a proxy should be used for this VPN connection. This can be set to automatic, manual, or disabled.
When using Systems Manager Sentry VPN security, the username and password used to connect to the client VPN are generated by the Meraki cloud. Usernames are generated based on a hash of unique identifier on the device and the username of that device. Passwords are randomly generated.
Was this article helpful?
Related Articles
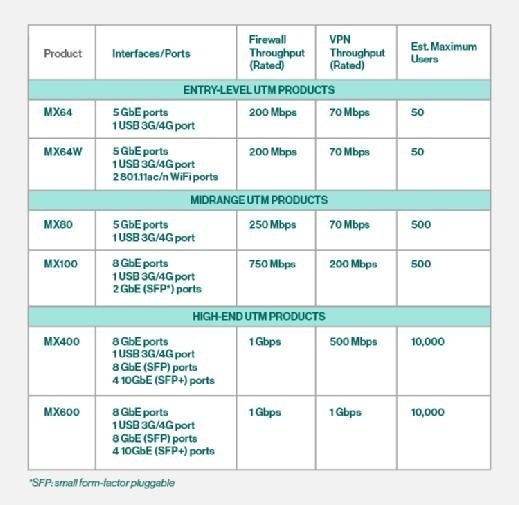
Cisco Meraki product lines offer various types of VPN options for small office and/or remote deployments. Each option is recommended for a different type of scenario, ranging from a single client, to several wired and wireless clients. If you have a complex requirement not covered below, please contact your Cisco Meraki account executive to discuss what would be the best fit for your particular needs. This article will discuss the scenarios listed below.
- Single Client VPN
- Wireless Client VPN
- Wired/Wireless Client VPN
Single Client VPN
Single client VPN would be particularly useful for clients utilizing mobile devices, laptops, as well as home desktop users. The Meraki Client VPN utilizes the native VPN client built into Windows, OS X, and iOS clients to name a few examples.
Client VPN creates a tunnel from the client and forwards all VPN traffic through that tunnel to the MX. The MX will then forward the traffic towards the destination. Each client that connects is placed on the subnet specified for Client VPN devices.
For a guide on configuring Client VPN on the MX and the client device, please refer to our Client VPN Configuration Page.
Wireless Client VPN
Note: This VPN only works with a Cisco Meraki MR Access Point.
Wireless Client VPN would ideally work when users want to utilize their wireless devices, or in an instance where there only are wireless clients in the environment. In this case the VPN SSID option is available; this option creates an SSID that will send all traffic through a VPN tunnel to either an MX Concentrator or VM Concentrator.
The wireless client will connect to the SSID like a standard wireless network, authenticate if necessary (WPA2-PSK, or 802.1x), and all traffic , or only VPN specific traffic (i.e. Split Tunnel VPN), will be sent through a VPN tunnel to a concentrator.
To configure the SSID please refer to our Teleworker VPN Configuration guide.
Wired/Wireless Client VPN
Wired/Wireless VPN would be best for a home or office that has both wired and wireless clients that need traffic sent over a VPN. The devices that support this are the Z-series Teleworker Gateways, MX60W, MX64W, MX65W, MX67W, MX68W, and MX68CW. Each of those units have both wired and wireless connectivity and can utilize the Site-to-Site VPN feature to forward both wired and wireless traffic to the remote VPN site. Any other MX appliance can also use Site-to-Site VPN, but a separate wireless access point would be necessary to provide wireless network access.
Wired clients would act as a normal client on the LAN until the traffic is received by the MX, then it will be encapsulated and sent over the VPN. Wireless traffic would be treated in the same way, once the client traffic is received by the MX it will be encapsulated and sent it over the VPN.
If split tunnel is configured, only traffic destined for the remote network will traverse the VPN. If full tunnel is enabled, Internet traffic will be sent over the VPN tunnel in addition to traffic destined for the remote network.
Meraki Vpn Device Free
For assistance setting up a site-to-site VPN, please refer to our Site-to-Site VPN Configuration guide.
